Article
A Simple Guide to Network Security
Learn the basics of network security, including the different types with examples
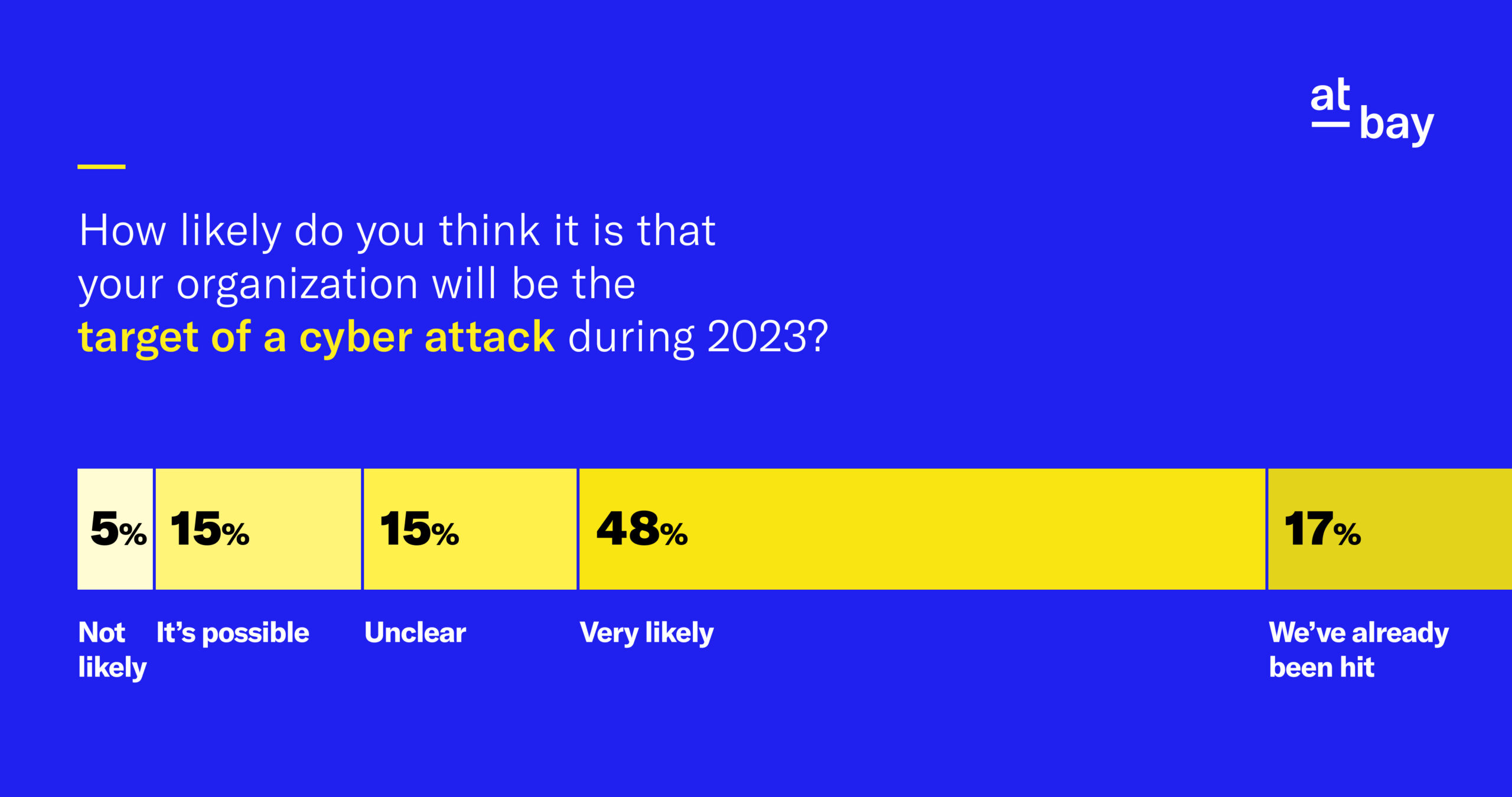
Whether you’re a seasoned IT professional or new to technology, understanding network security is essential in today’s corporate world. Network security is a fundamental pillar that protects sensitive data from being accessed, stolen, or corrupted by unauthorized users, thus ensuring the privacy and integrity of information. Additionally, robust network security measures help prevent operational disruptions and financial losses caused by cyberattacks or malicious activities.
What is Network Security?
Network security refers to the policies, procedures, and technologies designed to protect your network from unauthorized access, misuse, malfunction, or theft. It ensures that your data stays confidential and maintains its integrity while being readily available to authorized users.
Types of Network Security
There are various types of network security, each designed to serve unique protective functions.
Firewalls
Firewalls are a barrier between a private internal network and untrusted external networks, controlling incoming and outgoing network traffic. They monitor and control incoming traffic based on predetermined security rules. Additionally, firewalls can prevent the spread of threats across different parts of the network through segmentation, which further enhances internal security. They are a company’s first line of defense, blocking or allowing traffic to pass through.
Types of Firewalls
- Packet-Filtering Firewalls: Simple but effective, they inspect packets and prevent unauthorized access.
- Stateful Inspection Firewalls: More advanced, they track the state of active connections and make decisions based on the traffic’s state and context.
- Next-Generation Firewalls (NGFW): Combines traditional firewall technology with additional functionalities like encrypted traffic inspection and intrusion prevention.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
These systems monitor network traffic for suspicious activities and intrusions. They either alert you (IDS) or take action to block the bad traffic (IPS).
What’s the difference between an IDS and IPS?
An Intrusion Detection System (IDS) monitors network traffic for suspicious activity and alerts you when potential threats are detected, but it does not take action to stop them. In contrast, an Intrusion Prevention System (IPS) not only detects, but actively blocks or mitigates threats in real-time to prevent them from causing harm.
Virtual Private Networks (VPNs)
VPNs secure communication over the internet by encrypting data, providing a secure “tunnel” for remote users or branch offices to connect to the main network. These are widely used by businesses, with brands like Check Point Technologies and Palo Alto offering popular versions.
A company should be very careful about the VPN it selects for its security program. VPNs are frequently targeted by cybercriminals due to their inherent need to be accessible via the public internet, making them visible and thus more susceptible to potential attacks. The complexity of VPN systems also means they have multiple points of potential failure; misconfigurations, substandard management, or neglected software updates can create exploitable openings in a network’s defenses. You can read more about our philosophy on VPNs in At-Bay’s Knowledge Center.
Antivirus Software
These programs detect, prevent, and remove malware, protecting your systems from a variety of threats.
Antivirus software protects devices from malware infections by continuously scanning files, emails, and web activity for known malicious signatures and suspicious behavior patterns. It uses a combination of signature-based detection, heuristic analysis, and real-time monitoring to identify and eliminate threats, ensuring that your systems remain secure and operational.
While antivirus software was once the cornerstone of cybersecurity, it is now considered basic and somewhat outdated in the fight against sophisticated threats like ransomware. The signature-based detection means the software can only identify known malware by comparing files against a database of signatures. Organizations need more advanced and adaptive security measures, such as behavior-based detection and comprehensive endpoint protection, to effectively safeguard against today’s malicious actors.
Endpoint Detection and Response (EDR) software
Endpoint Detection and Response (EDR) is software that continuously monitors and collects data from network endpoints, or any device that is connected to your organization’s network, such as desktops, laptops, tablets and mobile phones, servers, or other devices that rely on an internet connection.
EDR software goes further than antivirus software, analyzing behavior and using machine learning to catch new or changing attacks. This means EDR can notice and stop threats that traditional antivirus might miss, keeping businesses safer in the face of changing and maturing threats.
Network Access Control
Network Access Control (NAC) is like a VIP list for your network. It ensures that only authorized devices and users can connect to a network by enforcing security policies and compliance checks. It works by verifying the security posture of devices, granting access only to those that meet predefined criteria, such as having up-to-date antivirus software and operating system patches.
Network Access Control is a fundamental part of “Zero Trust,” a security model that operates on the principle of “never trust, always verify” when it comes to any user or device. With Zero Trust, all users, devices, and activities must be authenticated and continuously validated before being granted access to resources. This approach minimizes security risks by eliminating implicit trust, ensuring strict access controls are applied consistently across the network.
Data Loss Prevention (DLP)
Data Loss Prevention (DLP) software protects sensitive information from being inadvertently or maliciously shared outside the organization by monitoring, identifying, and controlling data transfers. It works by scanning emails, file transfers, and other communications for predefined data patterns or compliance rules, and either blocks the transfer, alerts administrators, or encrypts the data to prevent unauthorized access.
Email Security
Email is the easiest way for cybercriminals to infiltrate your network. Email security tools help filter out phishing scams, malware, and spam, keeping your inbox and network safe from potential threats.
Secure email is especially important for businesses. Whether your business has 3 employees or 300, each person is a potential target for a cyberattack — and even one incident can cause irreparable damage.
Email security practices guard against a wide array of threats, ranging from phishing scams to ransomware attacks. A secure email gateway (SEG) can serve as a resilient shield, empowering businesses to carry out their operations with strengthened defense mechanisms and robust safeguards. We recently ranked email solutions and email security solutions with the highest to lowest frequencies of cyber incidents among At-Bay policyholders. You can read the full report here.
Is a Network Security Platform Necessary?
A Network Security Platform (NSP) offers a centralized, multifaceted approach to protecting your network from a wide array of cyberthreats. IT not only enhances your security posture but also ensures compliance, protects sensitive data, and supports business continuity. By integrating various security tools and functions into a single, cohesive system, an NSP provides a scalable and efficient solution to meet the evolving security needs of businesses of all sizes.
Best Practices for Network Security
Best practices for network security are crucial for protecting important data from cyberattacks. Following these practices can help reduce the chances of security incidents and keep network resources safe and reliable.
Use Strong Passwords That are Updated Regularly
Regularly updating your passwords helps prevent unauthorized access by making it harder for hackers to exploit old or weak passwords. To protect your passwords, you can use tools like password managers, which securely store and generate complex passwords, thereby reducing the risk of breaches. Password managers can institute best practices for passwords, which emphasize the importance of password length over complexity. Password managers can create longer passphrases, which offer greater security than shorter, intricate passwords.
Multi-factor authentication (MFA) strengthens passwords by adding an extra layer of security, requiring users to provide additional verification beyond just the password, such as a fingerprint or a code sent to their phone. This means even if a password is compromised, unauthorized access is still unlikely without the second form of authentication.
Regular Software Updates
Regular software updates improve network security by patching vulnerabilities that could be exploited by hackers, ensuring your systems are protected against the latest threats. These updates often include security enhancements and bug fixes, which work by closing gaps in the software that cybercriminals might use to gain unauthorized access.
Regular Backups
Data backups improve network security by ensuring that data can be quickly restored in the event of a cyberattack, hardware failure, or accidental deletion, minimizing downtime and data loss. They work by creating copies of your data at regular intervals, which are stored in secure, separate locations, so that even if the primary data is compromised, a clean and recent version is always available.
Additionally, regularly testing backups is essential to ensure that data can be successfully restored in the event of an attack. Quarterly tests can identify potential issues and gaps, and allow for timely adjustments to guarantee data integrity and availability when needed.
At-Bay research found that backups can help reduce the severity of claims — both in terms of cost and any downtime a business suffers. They can reduce total ransomware claim costs, mitigate recovery time, and potentially impact cyber insurance premiums.
Employee Training
Even the most advanced security system can fall victim to human error. Employee training improves network security by educating staff on cyberthreats, thus reducing the likelihood of mistakes that lead to security breaches. It works by providing regular instruction on best practices, such as identifying phishing attempts and proper handling of sensitive information, which collectively enhance the organization’s overall security posture.
How InsurSec Can Help With Network Security
Network security might sound complex, but think of it as a pillar of your business’s cybersecurity foundation. From firewalls to data backups, VPNs to EDR, employing a comprehensive security strategy will keep your network safe from threat actors. Remember to stay updated, educate your team, and always be prepared for potential threats.
All statements for At-Bay, Inc. companies.