Article
4 Key Takeaways From At-Bay’s 2024 InsurSec Report
An analysis from a year’s worth of claims and cybercrime data
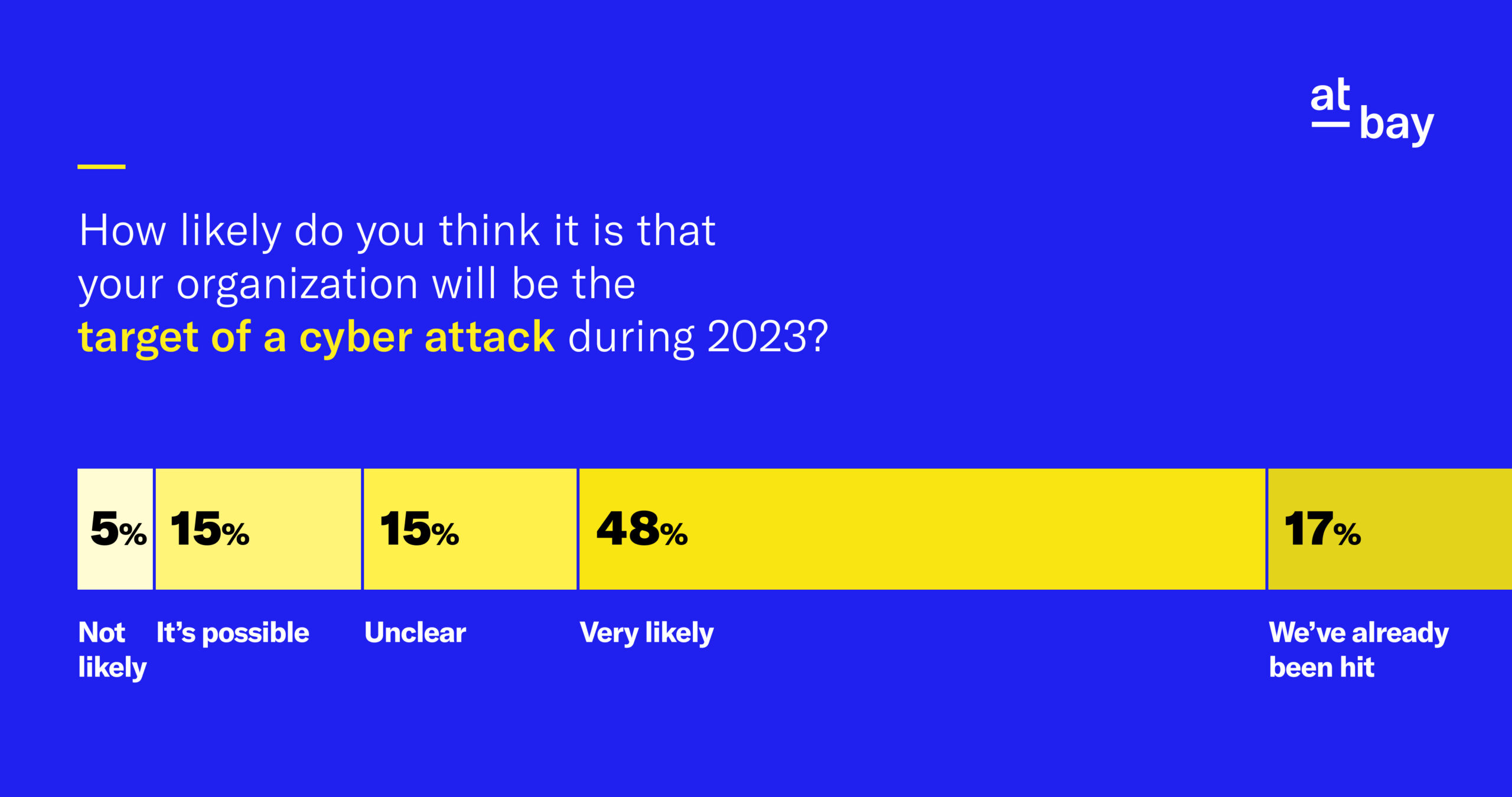
Looking back at 2023, one thing is clear: The threat of ransomware didn’t disappear, it just changed. Even though direct ransomware attacks only slightly increased compared to 2022, a larger volume of businesses experienced a cybersecurity incident.
Overall ransomware claims frequency rose 64% from 2022, mostly driven by a 415% increase in indirect ransomware (an incident where an organization is indirectly impacted by a cyber event on their vendor or partner).
Direct ransomware (a ransomware incident where an organization is directly targeted by a cyberattack) also rose 17%, including a 48% jump for the smallest companies in our portfolio (those with less than $25 million in annual revenue).
This dramatic rise in ransomware is at the heart of At-Bay’s first-ever InsurSec Report. Our inaugural review of our 2022 and 2023 claims and cybercrime data breaks down how threat actors are changing their methods, what’s really driving the cost of ransomware, and which technologies are leading to riskier outcomes for businesses.
Here are some of the key takeaways from our report — and what it means for businesses.
Double Leverage Attacks Return the Emphasis to Prevention
Our data showed that threat actors are combining encryption and exfiltration tactics to achieve what we call double leverage. In this type of attack, threat actors not only lock up a company’s files through encryption, they also steal and publicly release company data with exfiltration. This tactic significantly ramps up the pressure on affected businesses. In this situation, a business can no longer simply use backups to restore operations; they must also contend with the threat of leaked sensitive data.
More than half of all direct ransomware claims were double leverage attacks, and they were also the most costly to businesses: Combined encryption and exfiltration events saw the highest median ransom paid ($195K) over encryption-only incidents ($66K) or exfiltration-only incidents ($110K).
Backups are critical, but they can’t always save a business from the threat of exposed data due to an exfiltration event. So what can businesses do?
Staying ahead of attackers is a full-time job, and one which can be overwhelming for businesses that do not have the budget for in-house, dedicated IT and security teams. This is why Managed Detection and Response (MDR) services can be such a vital tool for small and medium-sized businesses. MDR can help businesses stay secure and reduce cyber risk at a fraction of the cost and hassle of hiring an in-house team.
According to At-Bay data, more than 50% of cyber claims could have been mitigated by an MDR. Using a combination of seasoned security experts and cutting-edge software, MDR services provide a layer of protection from threat actors and their evolving ransomware schemes.
Indirect Ransomware Is Increasing the Blast Radius: Cyber Insurance Critical for Both You and Your Vendors
Indirect ransomware (which we define as an incident where an organization is indirectly impacted by a cyber event on their vendor or partner), exploded by 415% in 2023, mostly thanks to the MOVEit incident. The vulnerabilities in the popular file transfer software led to a vast number of organizations being impacted, either directly or through the software supply chain, costing them thousands of dollars to recover and return to normal operations. The incident disrupted not just individual businesses, but entire sectors. Education and finance were among the hardest-hit industries.
Although the average indirect ransomware severity ($47K) was far below direct ransomware severity ($370K), the financial loss associated with indirect ransomware, particularly for small and mid-sized businesses, can still be a considerable burden. It’s also important to consider the collateral damage to a business, which may include long-lasting reputational damage or significant business interruption.
These attacks illustrate the growing need for businesses to vet third-party vendors’ security posture, including whether or not they have their own cyber insurance policies. In the event of a claim due to a vendor or partner breach, cyber insurance may cover an impacted organization’s loss, underscoring the importance of having robust coverage.
Businesses that experience an indirect ransomware attack may not be at fault and may be able to recoup losses from the organization that was initially attacked or from their cyber insurance provider.
Self-Managed VPNs Associated With Riskier Outcomes: Consider Cloud-Based Solutions
Remote access technologies continue to be a weak point in a company’s defenses, accounting for 58% of direct ransomware claims, by far the most targeted entry vector.
More specifically, self-managed VPNs, — those that are implemented and maintained on-premises by an organization’s own IT team — accounted for 63% ransomware events where remote access was the initial entry vector, a shift from the commonly-targeted RDP.
Two of the most popular self-managed VPNs, Cisco and Citrix, stood out for all the wrong reasons. Organizations using these VPNs were found to be 11X more likely to fall victim to a direct ransomware attack compared to those not using self-managed VPNs or opting for a cloud-managed solution.
The data backs previous warnings from our security experts: While VPNs are essential for modern business operations, the heightened risk associated with any self-managed VPN is large since they rely on outdated software, are easily misconfigured, and may be difficult to patch.
Ransoms Are Negotiable: Have an Incident Response Plan (and Strong Backups) Ready
In 2023, threat actors averaged a ransom demand of $1.26 million. However, once incident responders negotiated with attackers, the amount that businesses ended up paying was closer to $282,000. In fact, in 53% of claims, there was no ransom paid.
This is where the power of good backups comes in: If a business gets hit with ransomware, being able to recover the lost or locked data means a business may be able to avoid payment — or at the very least, reduce it. Our research found that firms that couldn’t get their data back from backups were 3X more likely to pay a ransom compared to those who could bounce back using their backups.
However, backups aren’t simply a plug-and-play technology. Organizations should understand how other factors — such as network bandwidth, data integrity, and system inventory — can impede restorations from a ransomware attack if not properly managed. Accounting for these factors will have an impact on how quickly an organization can resume normal operations and how much leverage you may have during negotiations.
Embracing InsurSec Can Help Businesses Avoid Catastrophe
Cyberthreats, particularly ransomware, are frequently evolving. Our report shows that businesses of all sizes are always at risk because threat actors are constantly finding new ways to exploit weaknesses in the software businesses frequently use. There is no single piece of technology that will drive bad actors away; they will just change tactics to stay ahead of defenses.
That’s why InsurSec is so important. By combining the prevention of security and the protection of insurance, companies can achieve better security and reduce risk. This is the power of the InsurSec model, helping small- and medium-sized businesses close the growing gap they have in security technology and management. And by bringing together security and insurance, we can provide clarity and transparency on drivers of risk, helping defenders, vendors and regulators better address growing cyber risks.
Click here to read the full report