Article
Reducing Risk: How Attack Surface Management Can Better Secure Your Organization
Best practices to mitigate cyber risk and reduce your business’ attack surface
As your organization builds its IT systems to meet its goals and demands, it’s easy to inadvertently introduce potential risk with every new software or service. Your business timeline may move faster than the ability to give due diligence to every new piece of technology, or you may lack the necessary resources or personnel to properly implement cybersecurity whenever new technology is introduced.
In order to reduce the risk of successful attacks by reducing the number of potential attack vectors, your organization should make attack surface management (ASM) part of your core security strategy.
Attack surface management — also known as attack surface monitoring — is a security practice that involves identifying, analyzing, and reducing the attack surface, which refers to the exposed and vulnerable areas that an attacker can target to compromise the security or functionality of a system. It’s a proactive approach to cybersecurity that focuses on exposed services, ports, and other points of access.
Components of Attack Surface Management
A successful attack surface management strategy incorporates several phases that ultimately lead to a reduction in risk.
1. Asset Inventory and Identification
This phase gathers lists of all hardware, software, and other IT assets such as servers, routers, switches, and other networking equipment. This should include the asset’s name, description, location, and any other relevant information or unique identifiers that can be used for cataloging purposes.
Once your organization has a list of its assets, this can be used as the foundation of your ASM system. The IT team can then monitor your systems by tracking the number of hours each asset is used, as well as any changes in performance or functionality. Additionally, as an organization’s IT system changes, the IT team will need a way to keep track of the changes.
2. Vulnerability Assessment and Scanning
This phase should be a proactive step that constantly monitors your assets and networks for vulnerabilities. Using a combination of manual and automated tools, this assessment strategy should include the frequency of scans, scan type, and scan scope. It’s also important to chart how to assess the severity of identified vulnerabilities and develop a plan to remediate them when found.
3. Patch Management and Remediation
This phase works in tandem with vulnerability assessment, but comes after. Organizations should identify and prioritize systems that require patching, test patches before pushing them in a production environment, then deploy the patches in a timely manner.
Best Practices for Effective Attack Surface Management
Establish a Baseline
An organization will need a way to measure the effectiveness of its ASM strategy. Those in charge should establish metrics and key performance indicators (KPIs) to measure, such as particular high-risk vulnerabilities to monitor, percentage of assets with up-to-date patches and security configuration, and number of assets exposed to the public internet. Prioritize assets that are most important to your organization’s operations and those that handle sensitive data.
Continuous Monitoring and Assessment
Security teams should use tools that can detect changes, misconfigurations, and new vulnerabilities in real time. An organization should investigate and address issues promptly once discovered. Prioritize vulnerabilities based on risk level and create plans to patch, upgrade, or isolate vulnerable assets. Teams should also track remediation progress.
Automation and Integration
An organization should use tools that can automatically scan for missing patches, download patches, and deploy them to endpoints. This reduces the manual effort required and speeds up the patching process.
Collaboration and Communication
An organization should make sure to inform all employees of how its ASM strategy will affect their ability to do their job. Make end users aware of upcoming patch deployments and the need for timely patching to maintain security. This helps gain cooperation and compliance. An IT security team will also need executive buy-in and support in order to secure funding and resources that will power your organization’s attack surface management plan.
Regular Training and Education
An organization’s IT security team should receive hands-on experience in identifying and patching vulnerabilities. This can include running vulnerability scanners and penetration testing tools on your own systems and practicing responsible disclosure when vulnerabilities are discovered.
Attack Surface Management Tools for Businesses
Popular attack surface management tools offer various features to help organizations identify, prioritize, and mitigate vulnerabilities and threats. While each tool may have its unique set of capabilities, some common features that distinguish them are:
- Asset inventory and discovery: Identifying, cataloging, and managing all the hardware and software resources within an organization’s network
- Vulnerability management: Identifying, assessing, and remediating security weaknesses or vulnerabilities in a system or network
- Continuous real-time monitoring: Persistent surveillance and analysis of network and system activities in order to detect, identify, and respond to potential threats
- Threat intelligence feeds: Information from various sources that serve as a warning to possible threats
- Assorted risk and compliance reporting: Information gathered to quantify exposure to potential security risks and adherence to regulatory standards
There are a number of popular vendors that offer both on-premise and cloud-based ASM tools. They include:
- SentinelOne Singularity Ranger (At-Bay policyholders receive complimentary evaluation licenses for the Singularity platform and a 35% or more discount if licenses are purchased within 30 days after evaluation.1)
- Axonius
- IBM Security Randori Recon
- Microsoft Defender External Attack Surface Management
There are also some solutions that focus specifically on small and medium-sized businesses (SMBs). They include:
You should also consider seeking out a cyber insurance provider like At-Bay that includes attack surface management as part of its policies. Learn more →
It is critical to consider how your organization’s unique needs and requirements will influence what ASM tool is right for you. Integration with other security tools, your organization’s need for automation, and your budget will all factor into what attack surface management tool is best.
Attack Surface Management Techniques
Irrespective of which tool you choose, there are certain techniques that are required for effective attack surface management. These techniques will enhance your organization’s program and ultimately lead to reduced risk of a severe cybersecurity incident.
Network Segmentation
Network segmentation improves the security of an organization’s network by breaking the network into smaller, isolated segments. By limiting the attack surface, organizations make it harder for attackers to move laterally across the network and easier for security teams to monitor and protect sensitive assets.
Implementing a more granular security architecture and implementing controls that are specific to certain segments helps organizations greatly reduce the risk of a cyber attack.
Access/Privilege Management
Access management (also called privilege management) ensures that only authorized individuals have access to information or resources that are essential to the organization.
When designed and executed properly, this can help to prevent unauthorized access to sensitive data while ensuring employees can easily access the core technology and information that they need to work efficiently.
Role-based Access Control (RBAC) Systems
RBAC assigns permissions and access based on the job function, which is typically defined in a directory service such as Active Directory. Each role or job function carries a set of permissions that define what the user is allowed to do.
By assigning permissions to a role instead of to individual users, the management of access control is much easier, since changes only need to be made to the role permissions when it changes.
For example, a company’s HR department may have access to sensitive HR-related data, such as employee salaries, while the Marketing department may only have access to marketing materials and social media accounts. Instead of managing access controls for each individual employee, RBAC can be used to assign the necessary permissions and access to each department.
Cyber Insurance and Attack Surface Management
Cyber insurance coverage and ASM tools can work in tandem to improve an organization’s overall cybersecurity posture. InsurSec providers like At-Bay that include attack surface management with their cyber insurance policies can help businesses better manage risk and mitigate the impact of potential attacks.
It’s important for organizations to carefully evaluate their risks and coverage needs in order to select the right insurance policy and attack surface management tools that suit their particular requirements.
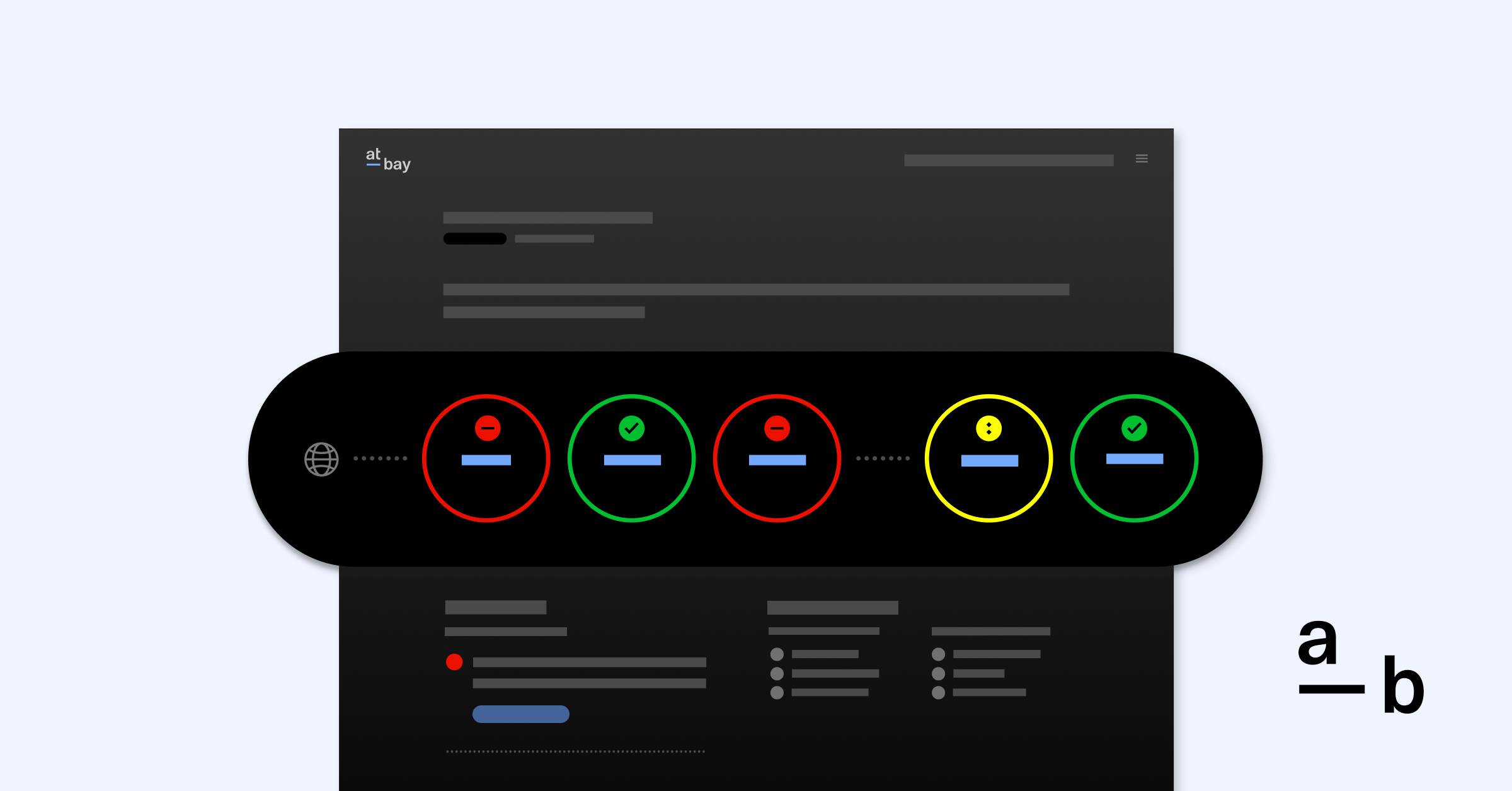
At-Bay combines insurance and security to help policyholders reduce their cyber risk, offering access to At-Bay Stance™ as part of our surplus Cyber and Tech E&O insurance policies.2 Our easy-to-use Stance dashboard helps policyholders manage their attack surface throughout their policy. It centralizes threat and vulnerability data from internal and external sources, evaluates and prioritizes areas of exposure, and empowers insureds to take action with clear recommendations from us.
Learn more about At-Bay Stance →
Footnotes
1. Policyholder is under no obligation to contract for services with any identified provider and is expected to conduct its own due diligence and assessment of the vendor, product, or services as appropriate for its needs. At-Bay does not endorse vendors or their services. Eligible policyholders may need to meet certain eligibility requirements to enter into an agreement with the vendor, as determined by the vendor.
2. At-Bay Stance is only available to At-Bay policyholders with Embedded Security, as shown in policy declarations. Please refer to your policy.