Article
BlackCat / Alphv Ransomware Group Exploits GoAnywhere Vulnerability With Higher-Than-Average Demands
At-Bay’s Cyber Research team confirmed today that a second ransomware group — the BlackCat (aka Alphv) group — has successfully exploited a known vulnerability in Fortra’s file transfer solution GoAnywhere MFT (CVE-2023-0669).
At-Bay’s Cyber Research team confirmed today that a second ransomware group — the BlackCat (aka Alphv) group — has successfully exploited a known vulnerability in Fortra’s file transfer solution GoAnywhere MFT (CVE-2023-0669). The high-severity vulnerability with a Common Vulnerability Score of 7.2 was first reported on February 1, 2023 as being exploited by the Clop ransomware group, which said it had compromised over 100 organizations that use Fortra’s file-transfer technology.
This latest exploitation of the GoAnywhere MFT vulnerability against a U.S. business by the highly-active BlackCat group raises the stakes on remediation. The vulnerability is a good example of how cyber criminals don’t just go after the most prevalent or publicly-known CVE disclosures. The most important indicator of risk isn’t just the score that’s given to the vulnerability, but how easily it can be exploited by cyber criminals in-the-wild, at scale, to achieve a desired outcome.
The primary reason ransomware groups like Clop and BlackCat choose to target GoAnywhere MFT is primarily to gain access to valuable data. Since GoAnywhere MFT solutions are designed to handle the secure transfer of sensitive data for organizations, compromising such a system could provide attackers with valuable information that they can encrypt and hold for ransom. These groups can then extract money from victims by threatening to withhold or expose their critical data.
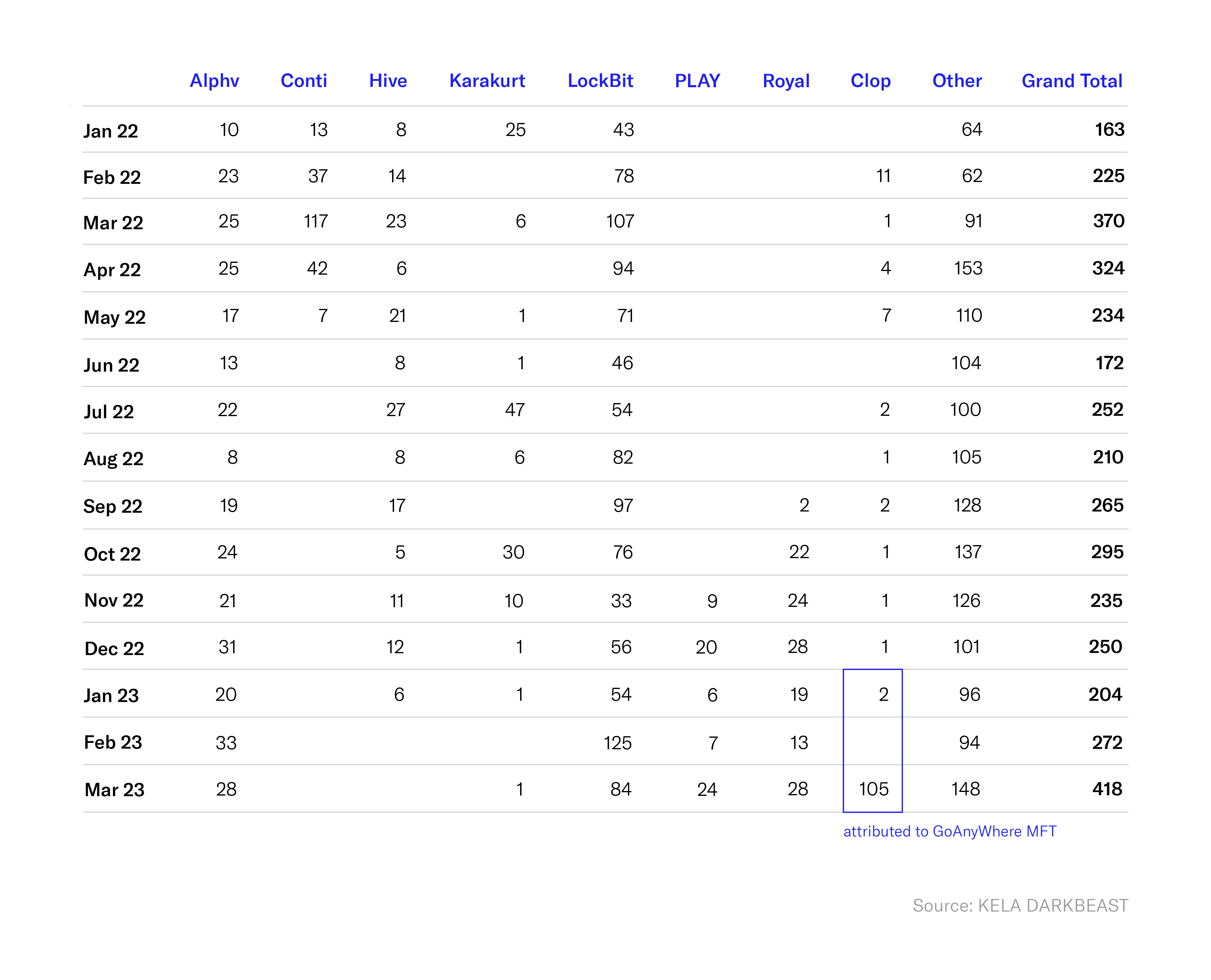
Source: KELA DARKBEAST
Timeline of the GoAnywhere Vulnerability’s Exploitation
On February 1, a zero-day vulnerability was discovered in Forta’s GoAnywhere Managed File Transfer (MFT) solution, which employs a licensing system with custom encryption to enable safer exchange of data between internal systems, business partners, and cloud services. When exploited, the vulnerability gave hackers complete control of the console and allowed them to execute code on all vulnerable instances. (According to Forta, successful exploitation requires administrative console access, and the Web Client interface itself is not exploitable.)
On February 7, a patch was released which required manual remediation.
On February 13, Community Health Systems — one of the largest U.S. healthcare providers with around 80 hospitals in 16 states — disclosed it had suffered a ransomware attack initiated through the GoAnywhere vulnerability. According to their report, approximately one million patients’ personal and health information was compromised. BleepingComputer reported that the gang has also been linked to ransomware attacks worldwide since at least 2019.
Today, At-Bay’s Cyber Research team confirmed that BlackCat — a well-known Ransomware- as-a-Service (RaaS) syndicate — has also successfully exploited the vulnerability and attacked a U.S. business in February 2023. The group started to make a name for itself in April 2022 with a sophisticated operation — carried out just a few months after the group emerged — which led to more than 60 companies being infected with its signature malware, and an FBI investigation.
By analyzing claims data, At-Bay’s Cyber Research team was able to find conclusive evidence that the initial point of entry was the GoAnywhere MFT vulnerability (CVE-2023-0669), and that the BlackCat group was responsible for the extortion event that followed shortly thereafter. (To read a technical analysis of the key details of At-Bay’s investigation, click here to jump ahead to that section below.)
The At-Bay Cyber Research team continuously monitors data leakage sites (DLS) associated with ransomware groups. These are sites where attackers publish information about their victims. A significant spike in activity from the Clop ransomware group was observed in March of this year which can be attributed to their targeting of GoAnywhere MFT. This highlights the importance of Active Risk Management (ARM), and underscores the necessity for daily Security Event Management (SEM) which includes identifying, evaluating, correlating and monitoring of system events and alerts.
Why is This Exploit Such a High Risk for GoAnywhere MFT Users?
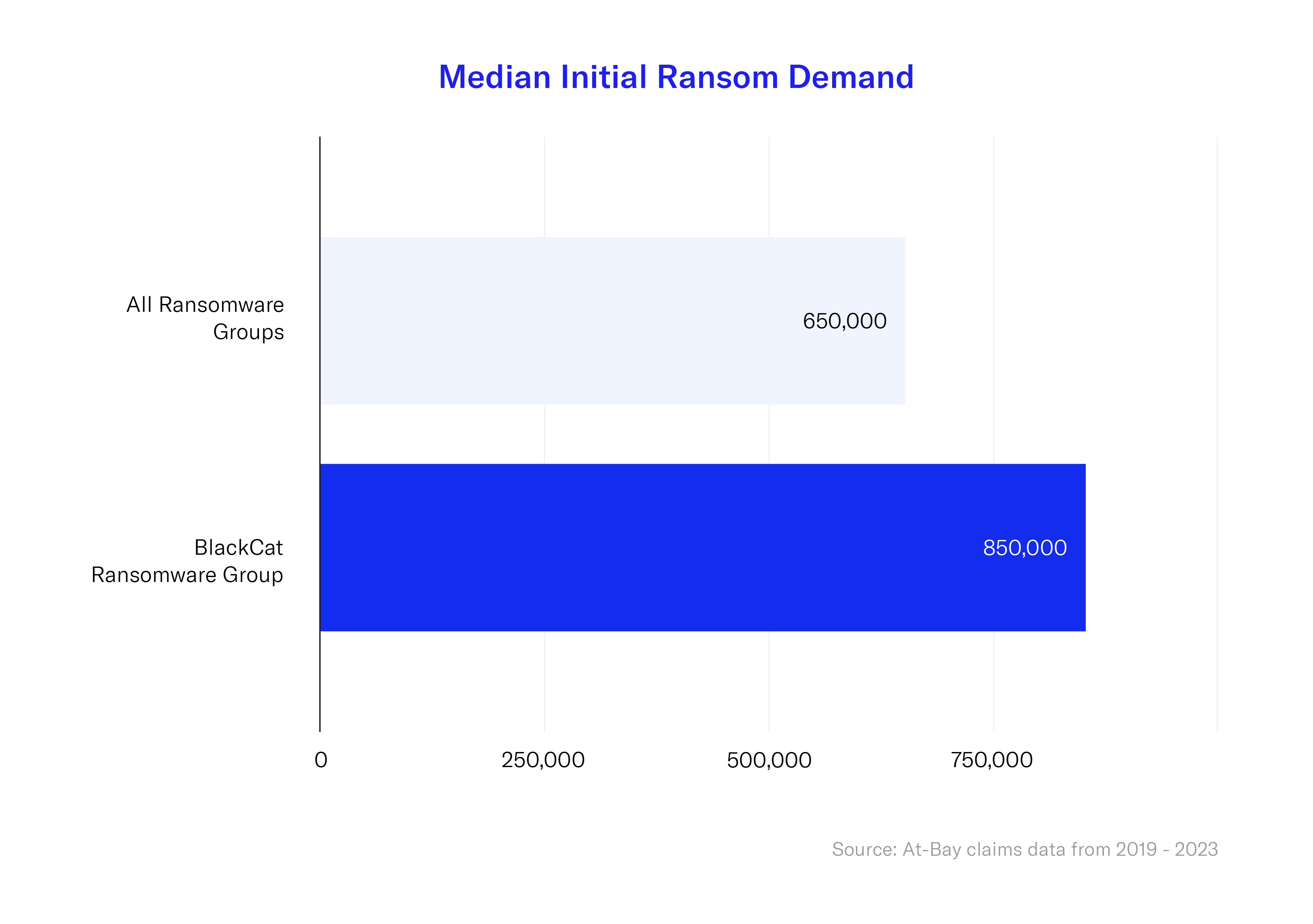
Our claims data indicates that the risk of exposure isn’t just higher for the GoAnywhere MFT vulnerability — because a second and highly active ransomware group is now involved — it could also be more costly. That’s because the median initial demand in ransom from the BlackCat group is higher than average.
Here’s are some other important details about this vulnerability and the ransomware group exploiting it:
1. BlackCat was the Third Most Successful Ransomware Group in 2022
According to At-Bay’s claims data — which includes any confirmed attacks against its 30,000+ policyholders — the BlackCat group was responsible for 9.8% of ransomware claims in 2022 making it the third most successful ransomware group last year. This year is trending similarly with 13.5% of ransomware claims in the first three months of 2023 coming from BlackCat.
Despite being a relative newcomer, BlackCat is also the third most active ransomware group so far this year following Royal (17.24%) and LockBit (37.9%).
Data from the last 15 months indicates that BlackCat continues to be a growing, persistent threat to businesses as one of the most successfully active groups.

2. Median Initial Demand for Ransom is Higher Than Average
Unit 42 reported that BlackCat is reportedly offering a higher return for affiliates via its ransomware-as-a-service, letting affiliates keep 80% to 90% of ransom payments, with the remainder going to the BlackCat author, which may also explain the group’s rapid growth. Unit 42 also reported that affiliates using BlackCat’s malware have been demanding as much as $14 million in bitcoin or monero, nearly three times the average ransom demand of $5.3 million asked for in the first half of 2021.
At-Bay claims data (from 2019 – 2023) confirms that the median initial demand from this group was higher than the average amount demanded by other ransomware groups.
3. GoAnywhere MFT Vulnerability is An Ideal Attack Vector for Ransomware
Executing a ransomware attack by targeting the GoAnywhere MFT vulnerability is extremely easy — with the exfiltration of data near certain, and the fast delivery of the payload also guaranteed. The vulnerability is a good example of how cyber criminals don’t only go after the most prevalent or publicly-known CVE disclosures. The most important indicator of risk isn’t just the score that’s given to the vulnerability, but how easily it can be exploited by cyber criminals in-the-wild, at scale, to achieve a desired outcome.
4. GoAnywhere MFT Users Fit the Ideal Business Profile for an Attack
Businesses who invest in an encrypted file transfer solution like GoAnywhere MFT obviously see a need to protect their data. Since ransomware relies on the extortion of sensitive business data in exchange for payment, it’s easy to see how this vulnerability is an attractive option for cyber criminals. Not only will they get privileged access to the console that houses sensitive data that businesses want to keep locked away, but the use of an encrypted file transfer solution indicates that the business places a higher value on their data than the average business that doesn’t encrypt it — making them an ideal target for ransom extortion.
5. Notoriety And Ease of Product Discovery Can Drive More Attacks
According to CISA, 13 out of the 15 top exploited vulnerabilities are typically found on servers with public IP addresses, because they allow hackers to easily identify a large number of vulnerable businesses to exploit after a simple scan of the internet.
When a vulnerable product that is outward-facing has few layers of defense separating it from the business’s internal network, while also being easy to identify, it has a higher likelihood of being breached. Additionally, attackers seem very likely to follow trends on vulnerabilities rather than specific products. For example, if a vulnerability suddenly gains traction on social media it is likely to be widely exploited within a very short span of time.
At-Bay’s Technical Analysis
Which GoAnywhere MFT Component is Affected?
The vulnerable component of GoAnywhere MFT is the admin portal, which is typically open on ports 8000 or 8001. It is strongly recommended that users — especially those whose admin portals are accessible from the internet — install the patch as soon as possible.
| Product | Affected versions | Fixed Versions |
| GoAnywhere MFT | Up to and including 7.1.1 | 7.1.2 and later |
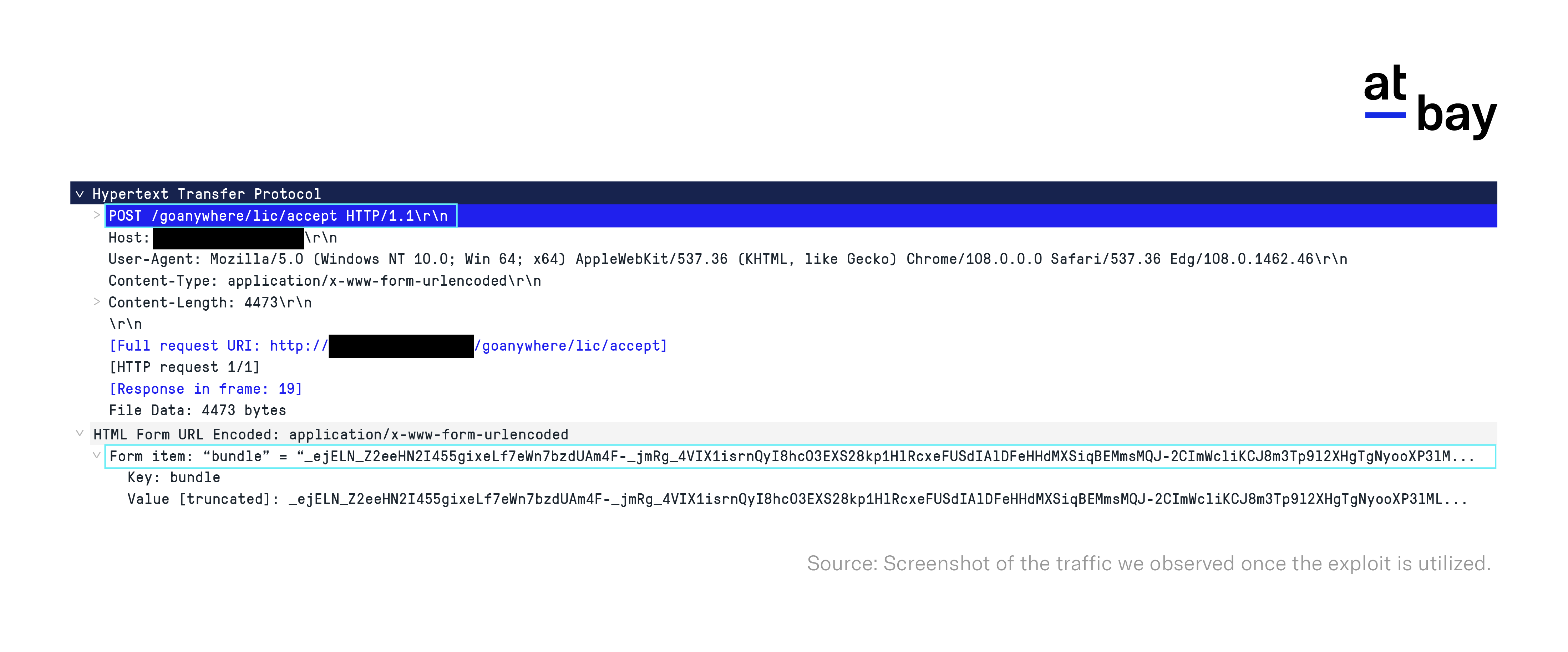
What Does the Exploit Traffic Look Like?
The vulnerability allows attackers to take advantage of a weakness in the License Response Servlet, which stems from the deserialization of an arbitrary object under the attacker’s control. We conducted tests on a susceptible machine and captured packet data (pcaps) of the traffic. The exploit is executed by sending a POST request to a specific path (“/goanywhere/lic/accept“) containing a serialized object payload (“bundle”) — a binary representation of an object that has been converted into a format suitable for easy storage, transmission, or reconstruction.
Notable Indicators of Compromise Associated with BlackCat
Based on our claims data, we observed communications originating from IP address 104.236.1.45 using port 8000. This IP address, hosted on Digital Ocean, appears to be scanning numerous IPs on port 8000, possibly in search of vulnerable GoAnywhere MFT instances. Furthermore, we identified that this IP communicated with Darknet IPs.
As a result, we strongly recommend blocking this IP address to mitigate potential risks.
What Actions Should Businesses Take Right Now?
Once At-Bay became aware of this exploit, we sent alerts to all our customers that were vulnerable. At-Bay is actively monitoring activity related to the GoAnywhere MFT vulnerability and working with our affected policyholders to help them quickly mitigate any risk. Please check that none of your products are vulnerable (refer to the “Which GoAnywhere MFT component is affected” section above), and patch them immediately. We urge businesses using any of the affected GoAnywhere MFT versions to immediately follow the mitigation methods recommended by Fortra.
If you have questions or other concerns regarding the GoAnywhere MFT vulnerability, please contact our Security team at security@at-bay.com.
*This article is for informational purposes only. No warranty is given or liability accepted regarding this information. The provisions, exclusions, terms, or conditions of the Policy and its endorsements control in all circumstances.