Article
How to Read Our Security Report
At-Bay’s security insights and recommendations can help businesses assess and reduce cyber risk.
You’ve received an insurance quote from At-Bay and included with it is a Security Report — what now?
You’ve come to the right place. We’ll walk you through everything you need to know step-by-step and explain how to read the At-Bay Security Report.
Follow along with your own Security Report or download our sample report for reference.
What Is A Security Report?
The Security Report is an in-depth analysis of a business’ current cyber risk. At the time of quoting a cyber insurance policy, we conduct a non-invasive perimeter scan of the business network to look for security issues and assess its cyber risk.
Our technology scans for dozens of known security issues and other controls that factor into a business’ overall cyber security posture. The findings are compiled into the report, which includes cyber insights, relevant industry data, and recommendations from the At-Bay Security Team.
What Security Issues Are You Looking For?
When assessing cyber risk, we take the same vantage point as a cyber attacker looking for a way inside a business’ network. Cyber criminals usually don’t target a specific business, rather they scan the internet for businesses that have certain vulnerabilities. When we find a security issue, we put our findings in the Security Report so it can be resolved quickly and effectively before it’s exploited by an attacker.
How To Read The Security Summary Page
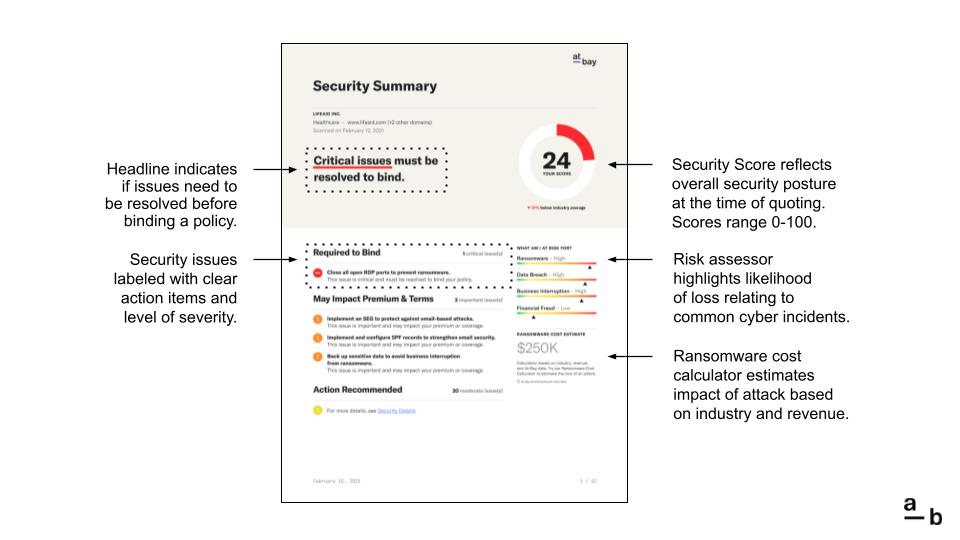
This is the Security Summary page. At the top of the page, you’ll see the business name, industry, primary website, and the date the Security Report was prepared. If the business has multiple websites, the report will indicate how many web domains were scanned.
The Security Score reflects the overall security posture of the business. A high score (green) means the business already has strong security controls in place. A moderate score (orange) means the strength of security can be enhanced, and a low score (red) means there are critical issues that must be resolved.
Security Issues are divided into three categories:
- Critical issues (red) must be resolved to bind a policy.
- Important issues (orange) may impact insurance premiums or coverage.
- Moderate issues (yellow) should be resolved to improve security, but are not mandatory.
The best way to improve a Security Score is to first resolve the critical issues, then the important issues.
The Security Summary page may not display every security issue. The total number of issues is listed to the right of each category. For a complete list of every security issue, flip ahead to the Security Details pages.
The Risk Assessor indicates the business’ exposure to 4 common cyber incidents, and the Ransomware Cost Estimate totals the numerous costs associated with a ransomware attack. You can use our Ransomware Cost Calculator to estimate the impact of an attack at any time.
How To Read The Top Security Issues Page
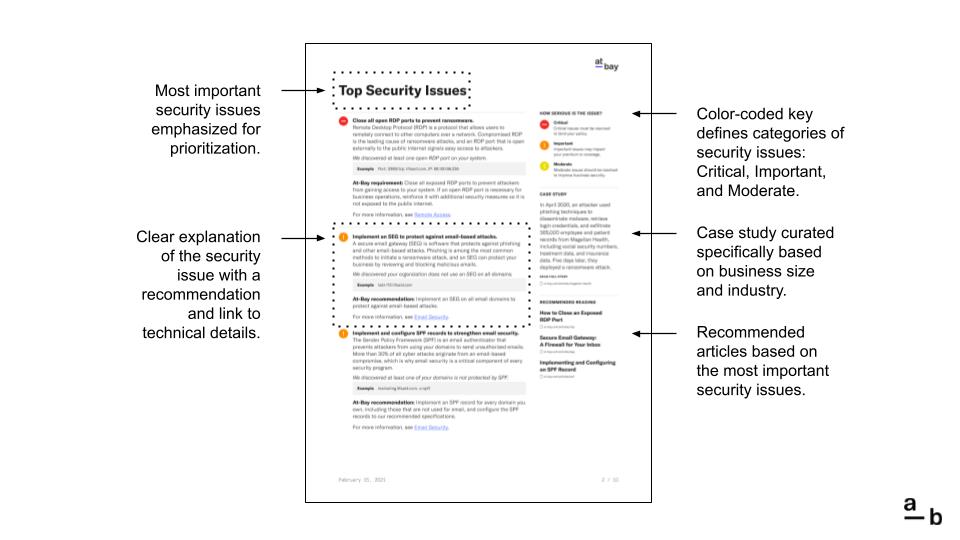
This is the Top Security Issues page. The most important issues are listed on this page, typically, an assortment of Critical and Important security issues.
Every security issue follows the same format:
- First, we explain what needs to be done and how it will help.
- Next, we provide a description of the issue and why it matters.
- Finally, we reiterate the action that will resolve the issue.
If it’s a Critical issue, this action is required. If it’s an Important or Moderate issue, the action is recommended. To learn more about what we discovered, click the hyperlink to jump ahead or go directly to the Security Details pages.
How To Read The Security Details Pages
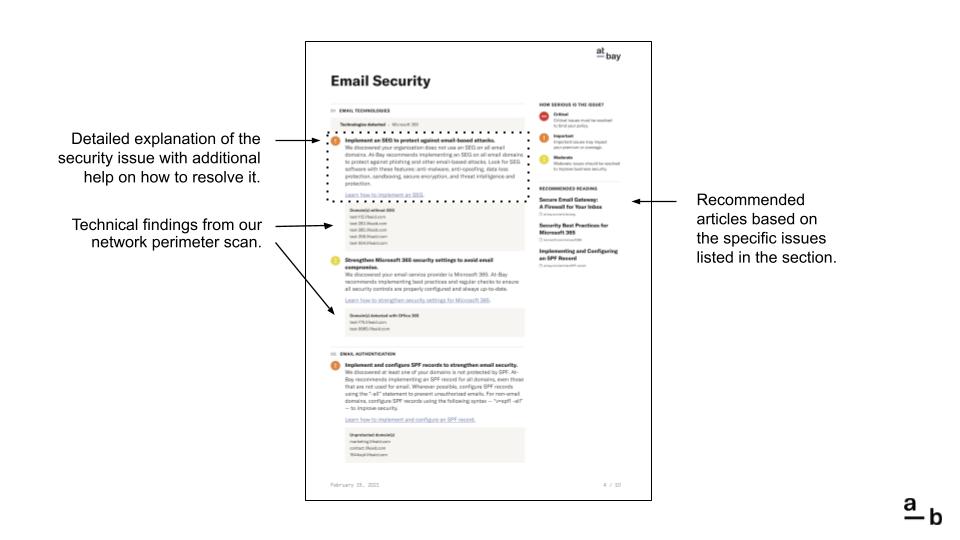
This is the Security Details page. The final pages of the Security Report are divided into one of five sections:
- Email Security
- Remote Access
- Network Security
- Access Controls
- Website Security
Each section has multiple categories. For instance, the Remote Access section contains categories for Ports and VPN, while the Access Controls section contains categories for Data Encryption, Data Backups, and Password Management.
Every security issue is accompanied by technical details and recommendations from the At-Bay Security Team. If the issue is related to the findings of our network perimeter scan, we provide the specific findings. We also provide an additional resource to help resolve the issue.
In the Security Details pages, the Recommended Reading contains resource articles that are specifically related to the issues listed on the page.
Have A Question That Isn’t Answered Here?
Start by turning to the last page of the Security Report and reviewing our Frequently Asked Questions. We also encourage you to read the Recommended Reading articles and other resources listed in the report.
If your question persists, please contact the At-Bay Security Team at security@at-bay.com.
Interested in learning more? Check out some of our popular articles:
- How to Close Exposed High-Risk Ports
- How to Implement a Strong Password Policy
- How to Strengthen Your Email Security Settings
Want a Security Report for your client? Get a quote on the Broker Platform today: