Article
Royal Ransomware: Likely First to Exploit Citrix Vulnerability In The Wild
Exploit used by Royal group to gain control of Citrix systems and launch ransomware attacks
On November 8, 2022, Citrix announced a new critical security flaw in its systems.
The vulnerability, identified as CVE-2022-27510, allows for the potential bypass of authentication measures on two Citrix products: the Application Delivery Controller (ADC) and Gateway. At the time of disclosure, there were no reported instances of the vulnerability being exploited in the wild.
However, as of the first week of 2023, At-Bay’s Cyber Research team gained new information that leads us to believe that the Royal ransomware group is now actively exploiting this vulnerability.
Why At-Bay Suspects Exploitation Of The Citrix Vulnerability
With our proprietary security scans and Active Risk Monitoring services, At-Bay regularly scans for any anomalous activity in vulnerabilities that we consider to be high-risk. As soon as the Citrix vulnerability was published, our Cyber Research team began assessing the magnitude of the risk and identifying businesses that might be exposed.
Data from our scans, information gleaned from claims data, and other intelligence gathered by our Cyber Research team point to the Citrix vulnerability CVE-2022-27510 as the initial point of access utilized by the Royal ransomware group to launch a recent ransomware attack.
How Is The Vulnerability Being Exploited?
The suspected exploitation method of the Citrix vulnerability by the Royal ransomware group is in line with the exploitation of similar vulnerabilities we have seen in the past.
It appears that Royal is exploiting this authentication bypass vulnerability in Citrix products to gain unauthorized access to devices with Citrix ADC or Citrix Gateway and launch ransomware attacks. Exploiting vulnerabilities in servers is one of the most common attack vectors for ransomware groups — especially critical infrastructure servers like those provided by Citrix.
However, what sets this instance apart is that the ransomware group is using the Citrix vulnerability before there is a public exploit.
What Is The Royal Ransomware Group?
The ransomware group known as Royal — which emerged in January 2022 and became the most actively operating ransomware group in November 2022 — is considered one of the most sophisticated ransomware groups. It uses creative and unusual techniques to breach networks (including using vulnerabilities before there is a public exploit, like in this case) and primarily targets companies in the U.S.
Ransomware groups have websites called data leak sites (DLS) where they publish the names of their victims in order to extort payment from them. The victims published by Royal indicate that the group primarily targets the manufacturing industry. However, it is important to note that not all of Royal’s victims are published on its DLS.
While At-Bay’s own data regarding Royal’s cyber activities is limited, our Cyber Research team advises that the Royal group is, in fact, industry agnostic and will attack companies opportunistically across industries.
Which Citrix Products Are Affected?
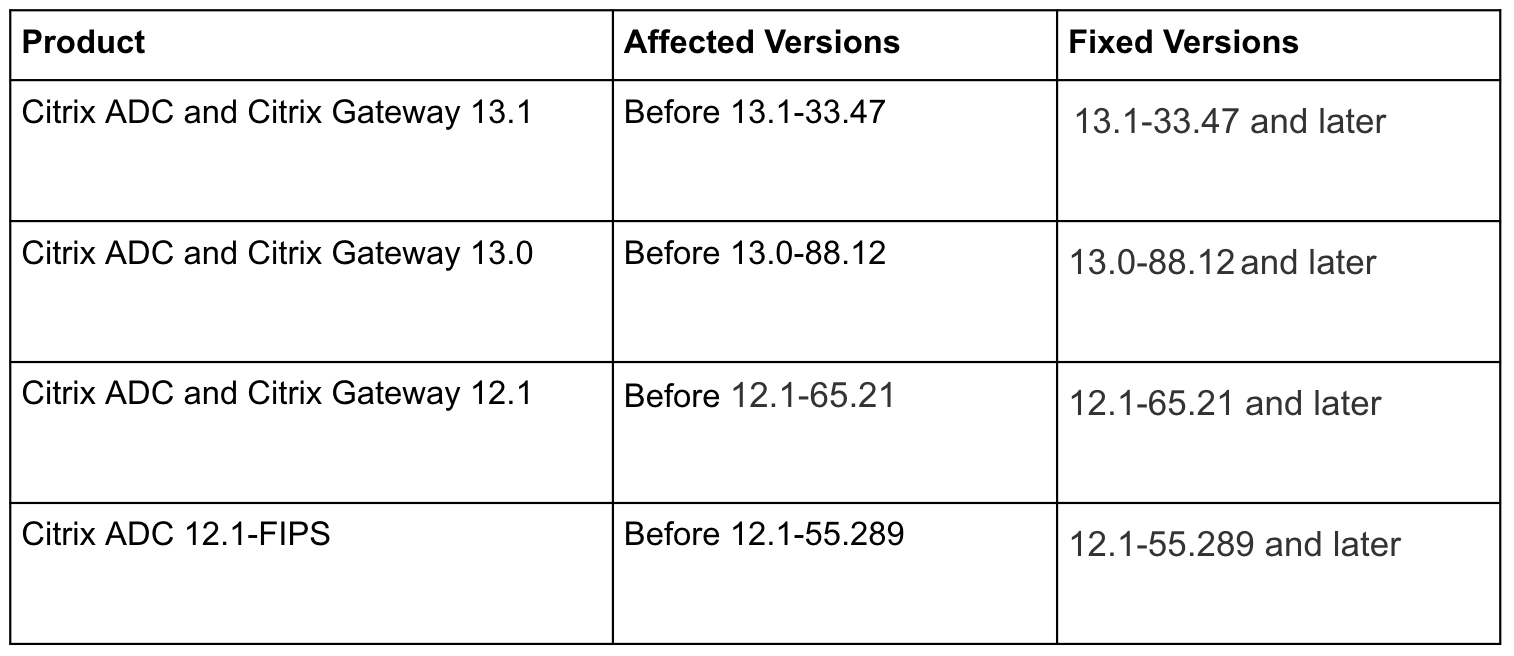
Citrix offers a variety of products for virtualization, networking, and cloud computing, which are used by many organizations and are known for their reliability and performance. The following versions of the Citrix ADC and Citrix Gateway are affected by the Remote Authentication Bypass Vulnerability (CVE-2022-27510):
What Actions Should Businesses Take Right Now?
At-Bay is actively monitoring activity related to the Citrix vulnerability and working with affected policyholders to help them quickly mitigate risk. We urge all businesses using any of the affected Citrix products to immediately patch the vulnerable software and follow the mitigation methods recommended by Citrix.
Even for clients who have not received a Security Alert, it’s important for them to check if they’re running vulnerable products and patch immediately.
If you have questions or other issues regarding the Citrix vulnerability, contact our Security team at security@at-bay.com.
This article is for informational purposes only. No warranty is given or liability accepted regarding this information. The provisions, exclusions, terms, or conditions of the Policy and its endorsements control in all circumstances.